Overview
Client VPN enables users to connect to their secure isolated network. Each account has their own isolated VPN service that is provided at no charge. This service is built into the platform and managed by the network operation center.
The initial configuration just requires a certificate to be downloaded and used for connecting to the VPN service. You can also configure two-factor authentication to require both a username and password. To learn more about ways to connect such as persistent VPN or direct connection, please review Network Access Options for Connecting to the Lumen Cloud Platform.
Current Limitations
There are only a few limitations on this service as it is based on the OpenVPN project.
- Maximum Concurrent Users: 19 (if you need more connections, review the different Network Access Options for Connecting to the Lumen Cloud Platform)
- Maximum Connection: 1Gbps
Getting Connected
In order to maximize resource efficiency on the platform, the Client VPN service will not be activated until after you have built your first server. Make sure you first deploy a server in order to have your VPN server activated.
Downloading VPN Configuration Files
-
Log on to the Control Portal. Using the left side navigation bar, click on Network > VPN.
-
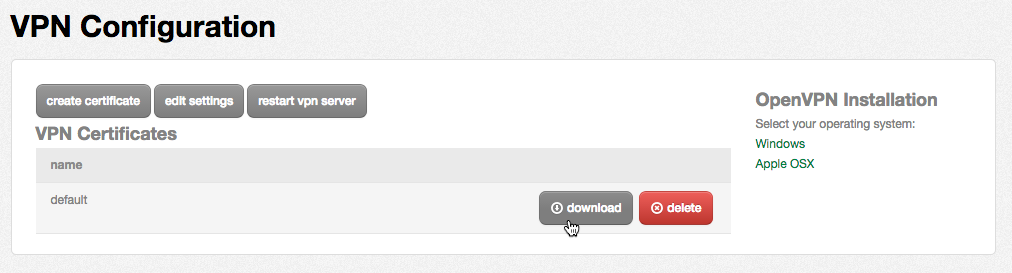
On the VPN Configuration page, find the existing VPN certificate and click the "download" button. (You may also use the "create certificate" button to create separate VPN certificates for other users.)
Installing the Client
How to Configure Client VPN – Windows
- Download and install the latest OpenVPN client for Windows
- Download the OpenVPN client from the OpenVPN client website. There is currently a known issue when using OpevnVPN client version 2.4.5 with OpenVPN servers provisioned prior to June 2017, to resolve use 2.3.18-I001-x86_64 bit release. Additional information can be found in our Troubleshooting Article.
- Double-click the installer and accept the UAC prompt.
- Accept all of the default options.
- Copy the downloaded OpenVPN configuration files into place
- Extract all of the files contained the downloaded zip file from the Control Portal. Allow it to create a directory named after the configuration.
- Navigate to the C:\Program Files\OpenVPN\config directory.
- Move the directory containing your configuration files out of Downloads and into the C:\Program Files\OpenVPN\config directory. Moving the whole directory will allow you to setup the ability to connect to multiple OpenVPN instances in the future, if necessary. Accept any prompts for administrative access to copy these files.
- Setup the OpenVPN GUI to always run as Administrator The OpenVPN GUI needs to be run as Administrator in order to properly set up additional routes in the routing table on your Windows PC.
- Press the Start button and navigate to the OpenVPN application folder (via All Programs or All Apps)
- If on Windows 8.1/10, right click on the OpenVPN GUI and select Open File Location
- Right click on the OpenVPN GUI and select Properties
- On the Properties screen, select the Shortcut tab, and click on the Advanced… button.
- On the Advanced Properties pop-up, select the checkbox for Run as Administrator. Click the OK button.
- Click the OK button on the OpenVPN GUI Properties pop-up.
- Click the Continue button to allow this change with Administrator permissions.
- Exit out of Windows Explorer.
- Right click on the OpenVPN GUI shortcut on your desktop and select Properties.
- Follow steps 4-7 to setup your desktop shortcut to always run as Administrator.
- Connect to your datacenter using the OpenVPN client
- Press the Start button and navigate to the OpenVPN folder. Click on OpenVPN GUI. Alternately, you can double-click on the OpenVPN GUI shortcut on your desktop.
- Accept the UAC prompt to run the OpenVPN GUI as Administrator.
- The OpenVPN GUI icon will appear in your System Tray. It will appear as a computer screen with a lock in front of it.
- Right click on the OpenVPN GUI and select Connect.
- The OpenVPN client will connect using your newly installed certificate.
- Once it successfully connects, it will minimize back to your System Tray.
- You are now connected to your home datacenter.
- Connect to servers
- Use the native Remote Desktop Client to connect to Windows servers.
- Download and install PuTTY to connect to Linux servers.
- Disconnect from OpenVPN
- Right click on the OpenVPN GUI icon in the system tray.
- Select Disconnect.
How to Configure Client VPN – Mac
- Download and install the latest Tunnelblick OpenVPN client
- Download the latest stable release from the Tunnelblick website.
- Double click the disk image (.dmg) to mount it
- Double click the Tunnelblick icon to install it.
- Click the Open button to accept the warning about opening downloaded files.
- Supply your Mac user account and password in order to install Tunnelblick into the Applications folder.
- After installation, click the Quit button to finish.
- Reboot your Mac so that the newly added kernel extensions will properly load.
- Copy the downloaded OpenVPN configuration files into place
- Extract the downloaded zip file from the Control Portal.
- Create a new folder in your Documents directory called tunnelblick_config.
- Copy the extracted configuration directory to the ~/Documents/tunnelblick_config folder.
- Navigate to the ~/Documents/tunnelblick_config/<config_dir> folder and double-click the .ovpn file.
- Click the Open button to accept the warning about opening downloaded files.
- Choose All Users or Only Me to add the configuration to Tunnelblick.
- Supply your Mac user account and password in order to add the configuration to Tunnelblick.
- Click on the Do not check for a change button to not check for public IP address changes.
- Select the Check Automatically button so that Tunnelblick will periodically check for updates.
- Connect to your datacenter using Tunnelblick
- Click on the Tunnelblick icon in the menu bar.
- Select Connect. You may get a pop-up window stating that 'ns-cert-type' was deprecated in OpenVPN 2.4 and removed in OpenVPN 2.5. It is safe to click the OK button to dismiss the pop-up. You should still be able to connect.
- The Tunnelblick icon will change to show you that you have successfully connected.
- If you get any warnings about public IP address not changing, you can click on the box for Do not check for IP address changes and then the OK button.
- Connect to servers
- Use the native Terminal app to ssh to Linux servers.
- Download and install an RDC client such as Microsoft Remote Desktop from the Mac App Store to connect to Windows servers.
- Disconnect from OpenVPN
- Click on the Tunnelblick icon in the menu bar.
- Select Disconnect.
- The Tunnelblick icon will change to show you that you have successfully disconnected.
How to Configure Client VPN – Linux
- As root, download and install the latest OpenVPN client and its dependencies
Ubuntu: apt-get install openvpn -y
RHEL/CentOS/Fedora: yum install openvpn –y
Note: For CentOS, you may need to also add the epel-release repo to yum
yum install epel-release - As root, copy the downloaded OpenVPN configuration files into place
- Extract the downloaded zip file from the Control Portal.
unzip default.zip - Copy the extracted configuration directory to the /etc/openvpn directory.
mv ./<config_dir> /etc/openvpn - Rename the .ovpn file to have a .conf extension in the /etc/openvpn/<config_dir> directory
mv default.ovpn default.conf - As root, connect to your datacenter using the OpenVPN client
- If you are using RHEL/CentOS/Fedora, export the following variable prior to starting the OpenVPN client. If you do not do this step, you will see the OpenVPN client connect, fail with a TLS handshake error and retry in an endless loop.
export OPENSSL_ENABLE_MD5_VERIFY=1 - Change directories to /etc/openvpn/<config_dir> and run openvpn command with the .conf file as your argument.
cd /etc/opevpn/<config_dir>
openvpn ./default.conf - You have successfully connected when you see the message “Initialization Sequence Completed”
- Connect to servers
- Use the native Terminal app to ssh to Linux servers.
- Use an RDC client to connect to Windows servers.
- Disconnect from OpenVPN
- Go back to the Terminal window where you started the OpenVPN client and type Control-C to disconnect.
FAQ
Q: After I select "Connect", my OpenVPN client never establishes a connection (or the icon does not turn "green"). What could be wrong?
A: Review the tips described in VPN Client Connection Troubleshooting.
Q: I have multiple sub accounts and want to be able to connect to each one's VPN individually. How can I do that?
A: By default, connecting to the VPN of a parent account will NOT provide access to the sub account networks as well. One option would be to Connect Networks Across a Parent & Sub-Account Hierarchy. This way, when you can log into OpenVPN on the parent account, you will be able to RDP/SSH to servers on the sub account network. Another option would be to maintain multiple OpenVPN connections on your machine. Please follow the steps describing how to Connect to Multiple OpenVPN Instances.
Q: Can I configure my VPN to require two-factor authentication?
A: Yes, just follow the steps describing how to Configure Two-Factor Authentication for Client VPN to require both a username and password along with the certificate.
Q: Is this service using secure SSL?
A: This service uses SSL certificates but does not run on the standard SSL port. In your configuration file (ends in OVPN) you can see the remote information such as: remote [IPHOST] [PORT] (example: remote 64.94.142.9 1194).
Q: Is this a shared or isolated service?
A: This is an isolated service for every account. Each account receives their own VPN instance to keep isolation and high security.
Q: Who handles the patching/maintenance of this service?
A: The platform handles all of the VPN instance patching and maintenance. Occasionally you will need to upgrade you VPN client application.
Q: What if I want to use my own VPN service?
A: There are two ways you can do this:
- If it is a physical device, you will need to have a persistent connection to your secure network. This will allow you to host a physical VPN server yourself and route across the persistent connection.
- If you would like to use a software-based VPN server, you can install it on a virtual server and configure the firewall rules to allow access. Many of our customers have done this but it will not be supported by the NOC.
Q: When I connect to the service, why can't I ping/connect to the server?
A: This is one of the most common issues with Windows and the OpenVPN client. Make sure to right-click on the application and selecting "Run as Administrator" when launching the OpenVPN client.
Q: Can I use this to connect to my office?
A: You cannot use it as a direct connect. To learn more about ways to connect such as persistent VPN or direct connection, please review Network Access Options for Connecting to the Lumen Cloud Platform.
Q: Do I need to install an OpenVPN server?
A: No, every customer account receives a dedicated OpenVPN server by default. Please note that it cannot be removed or disabled due to platform dependencies.